Our AI technology has developed highly reliable and robust PHP malware detection patterns by analyzing an extensive dataset comprising over 500,000 files of known malware code.
Overview
We are proud to offer our malware detection service, which provides reliable and robust detection patterns extracted by our advanced AI technology.
To ensure the highest level of accuracy and effectiveness, our detection patterns are regularly updated on a daily basis. We draw upon one of the world's largest databases of malware files, constantly incorporating newly discovered malware samples into our patterns. This proactive approach allows us to swiftly detect and mitigate the latest malware strains, providing you with up-to-date protection against evolving threats.
By integrating our API into your systems or applications, you can harness the power of our AI-generated detection patterns seamlessly. This enables you to perform real-time scanning and analysis, quickly identifying and neutralizing potential PHP malware infections.
Usage scenarios
What kind of services can the API be used for?
[Built into malware detection software]
Easily integrate our API into your server-side malware detection software and provide your clients with advanced protection.
[Real-time scanning of data uploaded by users]
Enable user-contributed sites to efficiently scan uploaded data for potential dangerous code, ensuring a safe and secure environment for all users.It will also prevent your service from being used as an intermediary source of malware, not only for users of your service, but for all internet users.
[Warns users of malware infection of their site]
Hosting services with multiple user sites, or multiple sites with maintenance contracts, can be inspected to provide early warning to users of site tampering or malware infection.
[Code-sharing services]
Empower security of code sharing services such as GIT, Subversion, and others to seamlessly identify the presence of malware within user-uploaded code, ensuring a secure and trustworthy environment for code collaboration and sharing.
[Text paste service (uploader)]
Empower text pasting services and file uploaders to efficiently detect and flag instances where users attempt to post malware code, ensuring a secure and trustworthy platform for content sharing and preventing the dissemination of harmful code.
Three types of Malware detection API are provided
Obtaining reliable malware detection patterns.
1146 detection patterns being distributed now.
It is the most reliable and balanced malware detection pattern acquisition API.
The API provides versatile malware detection patterns that can be applied to a wide variety of applications.
It provides a small number of highly selective malware detection patterns that can detect malware most efficiently with high detection accuracy. Files containing these patterns are very likely to be malware.
The adoption of this API pattern is recommended for the efficient analysis of huge amounts of data and its routine data analysis.
Newly added detection patterns.
919 detection patterns being distributed now.
This API prioritizes freshness of malware detection patterns.
While it may sacrifice some reliability, it excels at identifying files potentially harboring the latest prevalent malware.
If your objective is to detect the most recent malware, this API is the ideal choice. It inludes newly added malware patterns within a few months, although the possibility of false positives exists.
Maximum number of detection patterns
4568 detection patterns being distributed now.
The malware detection patterns available via this API provide the highest volume of malware detection patterns, including those extracted from malware-infected files from the last five years and the latest detection patterns.
If your objective is a thorough malware scan, this API is the perfect choice. However, be aware that may result in false positives.
Due to the extensive number of malware patterns it encompasses, this API can be resource-intensive and time-consuming when inspecting large amount of files. It is particularly recommended for deep inspection of folders suspected of malware infection, single-file analysis, or when specifically aiming to prevent malware infection within small groups of files.
Compromised accessing IP
10312 IP being distributed now.
In addition, we have detected unauthorised access and hacking attacks from over 30,000 sites, and we also provide an API of the ip addresses of dangerous hackers who are currently active.
With this API, you can obtain the IPs of unauthorised access sources that have recently been active in hacking activities, which are updated on a daily basis.
Structure of JSON data delivered by the API.
The malware patterns and attacker IP addresses that can be retrieved by the API are JSON data in encoded arrays.
NOTICE:The malware detection pattern is only updated once a day. API calls made more than once a day will retrieve the same data. To avoid server load, API calls are limited to once every 30 seconds. For this reason, please avoid excessive data retrieval by recording the data retrieved by the API in a database or by other means.
Malware pattern API
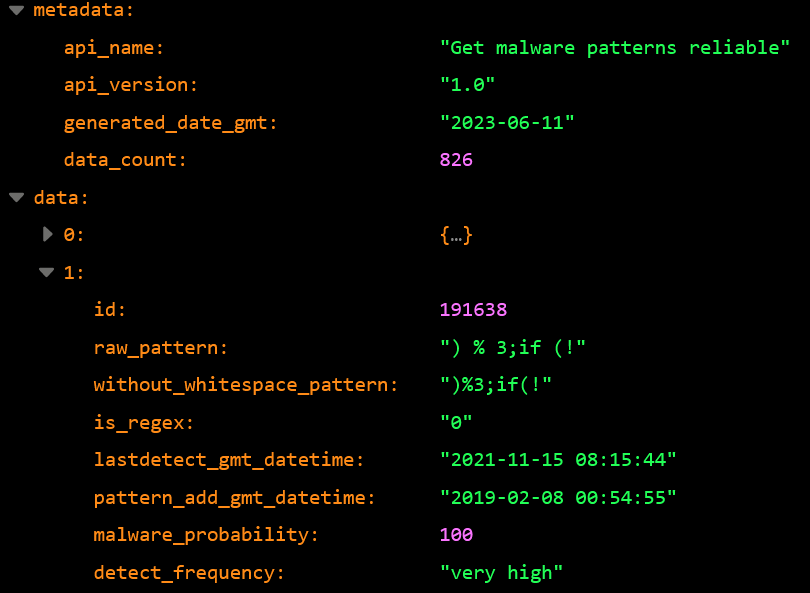
The JSON data that can be obtained via the API is divided into a metadata part, which indicates the version and name of the data, and a data part containing the actual detection pattern.
- id:The ID of the malware detection pattern.
- raw_pattern: The malware detection pattern extracted directly from the code.
- without_whitespace_pattern: Malware detection pattern without whitespace.
- is_regex: Flag to indicate whether the pattern is a regular expression detection pattern or not (0 or 1).
- lastdetect_gmt_datetime: date of last detection
- pattern_add_gmt_datetime: date when the detection pattern was added
- malware_probability: probability that the code containing this detection pattern was actually malware (%)
- detection_frequency: The detection frequency of this pattern (undefined,low,medium,high,very high).
NOTE:When using this API, we recommend that you remove whitespace from the code you want to scan and use without_whitespace_pattern for detection.
API of the compromised accessing IP
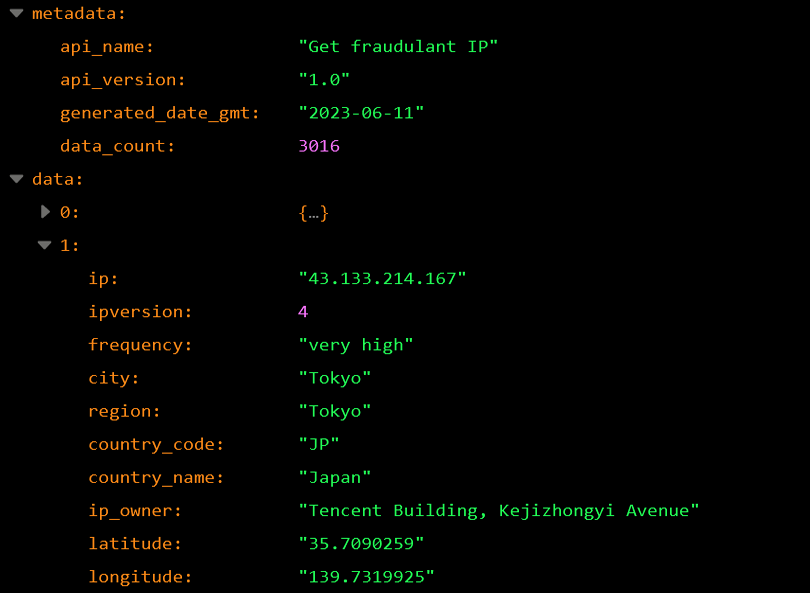
The JSON data that can be retrieved via the API is divided into a metadata part, which indicates the version and name of the data, and a data part, which contains the actual IPs.
- ip:IP address of the unauthorised access
- ipversion: IP version
- frequency: Frequency of attacks (undefined,low,medium,high,very high)
- city: Location of the IP (city)
- region: Location of the IP (state)
- country_code: Location of the IP (Country code)
- country_name: Location of the IP (country)
- ip_owner: Company or organisation that owns the IP
- latitude: Longitude of the IP
- longitude: Latitude of the IP
NOTE:Data other than IP address and IP version may be undefined.
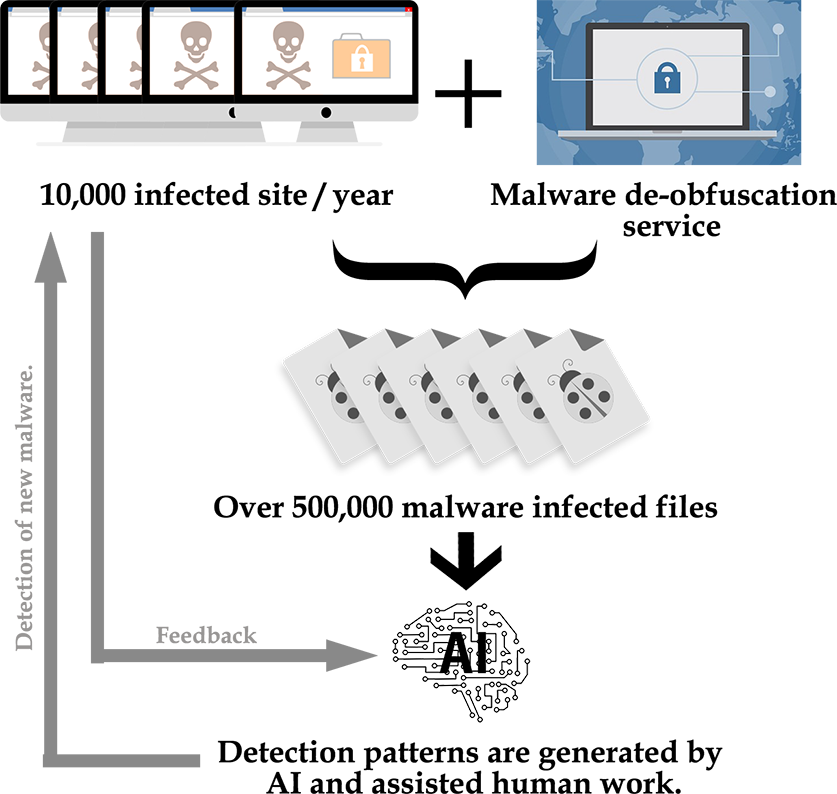
How are malware detection patterns generated?
1. We collect data on malware code from over 10,000 malware-infected sites per year, mostly WordPress, and PHP and JAVASCRIPT deobfuscation services.(We currently have over 500,000 files of malware code detected from over 30,000 sites.)
2. AI extracts robust, highly reliable malware detection patterns.
3. We actually inspect and detect malware files using the detection patterns described in 2. and provide feedback to improve their accuracy and reliability.
Pricing
Attacker IP acquisition API
-
Data updated once every 24 hours.
-
IP lists of unauthorised accessors collected from 30,000 sites via API.
-
Location data and country data of the attacker’s IP includes.
-
Data on attack frequency of attacker IPs includes.
10-day free trial
API for malware detection
-
Data updated once every 24 hours.
-
Detection patterns generated from 30,000 infected sites and over 500,000 files of malware.
-
Highly accurate and reliable malware detection pattern acquisition API.
-
API for acquiring the latest malware detection patterns.
-
API for acquiring more malware detection patterns, including older patterns.
-
Malware probability data per pattern.
-
Detection frequency data per pattern.
10-day free trial
Malware detection + attacker IP API
-
Data updated once every 24 hours.
-
Detection patterns generated from 30,000 infected sites and over 500,000 files of malware.
-
Highly accurate and reliable malware detection pattern acquisition API.
-
API for acquiring the latest malware detection patterns.
-
API for acquiring more malware detection patterns, including older patterns.
-
Malware probability data per pattern.
-
Detection frequency data per pattern.
-
IP lists of unauthorised accessors collected from 30,000 sites via API.
-
Location data and country data of the attacker’s IP incudes.
-
Data on attack frequency of attacker IPs includes.
10-day free trial
ABOUT US
We, BLUEGARAGE Inc. are at the forefront of web security in Japan.
BLUEGARAGE Corporation, established in 2015, has been dedicated to addressing website security concerns since its inception. Over the years, we have successfully restored numerous websites infected with malware, amassing valuable knowledge and data in the process.
Our release of WP-Doctor Malware scanner has the largest market share of any WordPress malware detection plugin released by a Japanese company. Our research indicates that it boasts the highest accuracy in malware detection globally, offering exceptional performance. Furthermore, we have meticulously collected and analyzed malware and security data from tens of thousands of websites that have installed this plugin, culminating in the release of our PHP malware detection API.
Although we cannot reveal the names due to confidentiality agreements, our knowledge has been highly effective and trusted by some of Japan’s largest listed companies, government agencies and organisations, and major hosting companies through consulting, software (plug-ins) provision and maintenance contracts.
Our mission is to increase the overall safety of websites by providing high security and the means to combat malware and unauthorised access, not only for large corporations and governments, but also for everyone (even for private websites and private tuition sites).
Contact
Contact US
- wpdoctorsales[@]gmail.com
- 1-5-8 Minamiazabu Minatoku Tokyo, Japan
