Introdoction
The PHP malware detection pattern API provides patterns for string searches that most efficiently detect malware extracted from the data of malware-infected files. There are two types of detection patterns: string or regular expression type, with regular expression type patterns accounting for approximately 20% of the total.
Api call
The data that can be obtained via the API is JSON data in an array containing malware detection patterns. It can be obtained by calling the following URL with a GET request.
https://api.website-malware-removal.com/v(API version)/?api=(API name)&accesskey=(key to access the API)
(API version) Only version 1.0 of the API version is currently available.
(API name)The following four API names are provided
get_malware_patterns_reliable
get_malware_patterns_new_addition
get_malware_patterns_full
get_fraudulent_ip
(key to access the API)The accesskey specifies the access key issued by the website to members with a paid subscription.
An example URL for an API call specifying the above query is shown below
https://api.website-malware-removal.com/v1.0/?api=get_malware_patterns_reliable&accesskey=1234567890abcdefgrh
Differences and description of each API
1.Obtaining reliable malware detection patterns.(get_malware_patterns_reliable)
Api call url example
https://api.website-malware-removal.com/v1.0/?api=get_malware_patterns_reliable&accesskey=1234567890abcdefgrh
The malware detection patterns that can be retrieved with this API are suitable for all applications.
If you want to analyse large amounts of data at high speed, or if you regularly analyse such data, you should use this API.
Detection accuracy is high and the likelihood of a file containing this pattern being malware is very high. This makes it the most reliable and balanced malware detection pattern acquisition API.
2.Newly added detection patterns.(get_malware_patterns_new_addition)
Api call url example
https://api.website-malware-removal.com/v1.0/?api=get_malware_patterns_new_addition&accesskey=1234567890abcdefgrh
The malware detection patterns that can be retrieved with this API are focused on newness.
This API is suitable for detecting files suspected of containing the latest prevalent malware, even if they are somewhat less reliable.
Use this API if you want to detect the most recent malware.
This API contains the most recent malware patterns added within a few months, but it is also possible to get false positives.
3.Maximum number of detection patterns(get_malware_patterns_full)
Api call url example
https://api.website-malware-removal.com/v1.0/?api=get_malware_patterns_full&accesskey=1234567890abcdefgrh
The malware detection patterns that can be retrieved with this API include more old detection patterns that have been detected within the last five years, rather than relatively new additions.
Use this API if you want to scan for malware in deeply. However, it also includes more recent and somewhat less reliable patterns, which may lead to false positives.
As this pattern contains a very large number of malware patterns, it can be server-intensive and time-consuming to inspect large numbers of files. It is recommended for deep inspection of folders with suspected malware infection, single-file inspection or for groups of files where you specifically want to prevent malware infection.
4.Compromised accessing IP(get_fraudulent_ip)
Api call url example
https://api.website-malware-removal.com/v1.0/?api=get_fraudulent_ip&accesskey=1234567890abcdefgrh
In addition, we have detected unauthorised access and hacking attacks from over 30,000 other sites, and we also provide an API of listing IP addresses of dangerous hackers who are currently active. With this API, you can obtain the IPs of unauthorised access sources that have recently been active in hacking activities, which are updated on a daily basis.
Data structure
Malware pattern API data structure
NOTE:The structure of the data that can be retrieved in the three api’s (get_malware_patterns_reliable, get_malware_patterns_new_addition, get_malware_patterns_full) is the same.
The JSON data that can be obtained via the API is divided into a metadata part, which indicates the version and name of the data, and a data part containing the actual detection pattern.
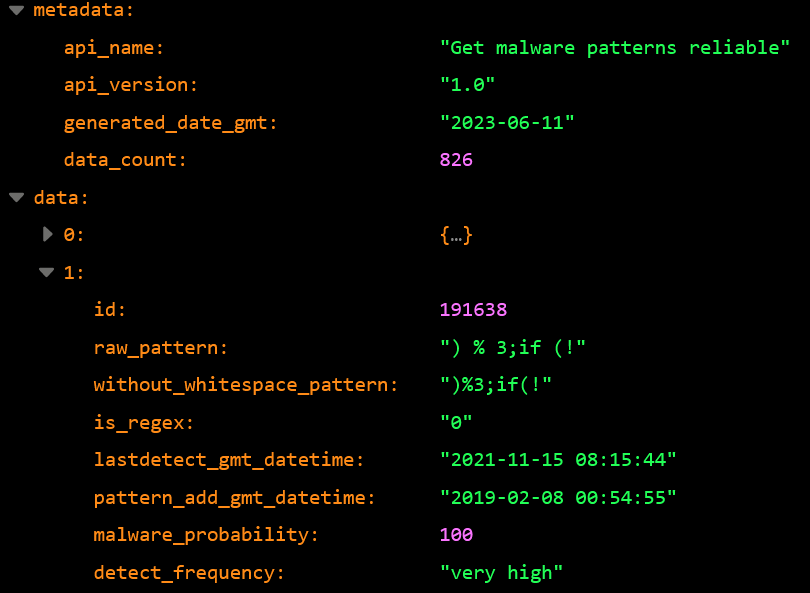
metadata
- api_name:API name
- api_version:Version of the API
- generateddate_gmt:Date this data was generated
- data_count:Number of data (malware detection patterns) included
data(Array)
- id:The ID of the malware detection pattern.
- raw_pattern: The malware detection pattern extracted directly from the code.
- without_whitespace_pattern: Malware detection pattern without whitespace.
- is_regex: Flag to indicate whether the pattern is a regular expression detection pattern or not (0 or 1).
- lastdetect_gmt_datetime: date of last detection
- pattern_add_gmt_datetime: date when the detection pattern was added
- malware_probability: probability that the code containing this detection pattern was actually malware (%)
- detection_frequency: The detection frequency of this pattern (undefined,low,medium,high,very high).
API of the compromised accessing IP data structure
The JSON data that can be retrieved via the API is divided into a metadata part, which indicates the version and name of the data, and a data part, which contains the actual IPs.
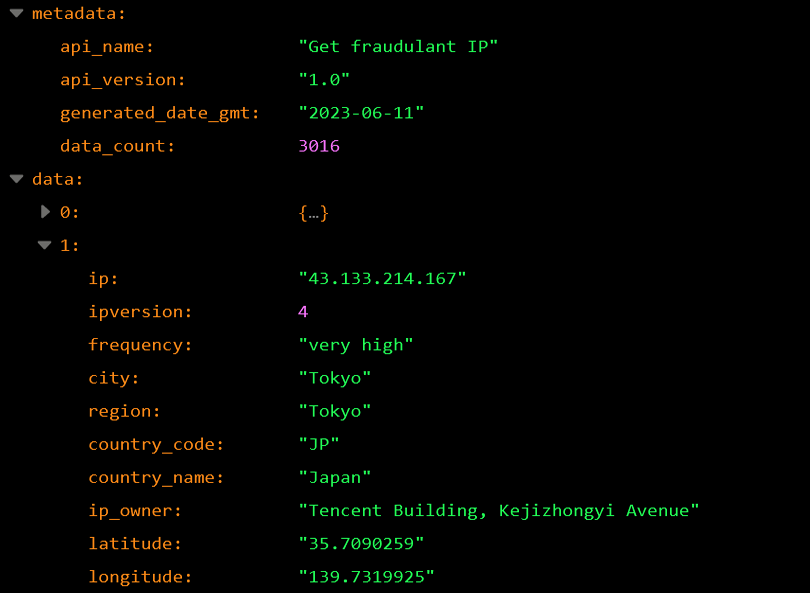
metadata
- api_name:API name
- api_version:Version of the API
- generateddate_gmt:Date this data was generated
- data_count:Number of data (IP) included
data(Array)
- ip:IP address of the unauthorised access
- ipversion: IP version
- frequency: Frequency of attacks (undefined,low,medium,high,very high)
- city: Location of the IP (city)
- region: Location of the IP (state)
- country_code: Location of the IP (Country code)
- country_name: Location of the IP (country)
- ip_owner: Company or organisation that owns the IP
- latitude: Longitude of the IP
- longitude: Latitude of the IP
NOTE:Data other than IP address and IP version may be undefined.
Sample code
Periodically call the API to retrieve and store data.
The code to retrieve the data via the API and store it in a text file on the server is shown below. Such code should be called periodically in CRON.
Note: Our data is only updated once a day, so it is not necessary to call API more than once a day.
<?php
$apiname = "get_malware_patterns_reliable";
$apiversion = "1.0";
$accesskey = "*******************************";
function call_api_save_as_text($apiname,$apiversion,$accesskey){
$apiurl = "https://api.website-malware-removal.com/v".$apiversion."/?api=".$apiname."&accesskey=".$accesskey;
$apidata = file_get_contents($apiurl);
$apidata_decode = json_decode($apidata);
preg_match('/([0-9])\d+/',$http_response_header[0],$matches);
$responsecode = intval($matches[0]);
if($responsecode != 200){
if(isset($apidata_decode->api_error)){
echo $apidata_decode->api_error;
}else{
echo "unknown error";
}
return;
}
$exportfilename = __DIR__."/".$apiname.".json";
file_put_contents($exportfilename, $apidata);
echo "Successfully saved API json file - Data count:".$apidata_decode->metadata->data_count;
}
call_api_save_as_text($apiname,$apiversion,$accesskey);
?>import json
import urllib.request
import socket
def call_api_save_as_text(apiname, apiversion, accesskey):
apiurl = f"https://api.website-malware-removal.com/v{apiversion}/?api={apiname}&accesskey={accesskey}"
with urllib.request.urlopen(apiurl) as response:
apidata = response.read().decode('utf-8')
responsecode = int(response.getcode())
if responsecode != 200:
apidata_decode = json.loads(apidata)
if 'api_error' in apidata_decode:
print(apidata_decode['api_error'])
else:
print("unknown error")
return
exportfilename = f"{apiname}.json"
with open(exportfilename, 'w') as outfile:
outfile.write(apidata)
apidata_decode = json.loads(apidata)
print(f"Successfully saved API json file - Data count: {apidata_decode['metadata']['data_count']}")
apiname = "get_malware_patterns_reliable"
apiversion = "1.0"
accesskey = "*******************************"
call_api_save_as_text(apiname, apiversion, accesskey)
import java.io.BufferedWriter;
import java.io.FileWriter;
import java.io.IOException;
import java.io.BufferedReader;
import java.io.InputStreamReader;
import java.net.HttpURLConnection;
import java.net.URL;
import com.google.gson.JsonObject;
import com.google.gson.JsonParser;
public class Main {
public static void main(String[] args) {
String apiname = "get_malware_patterns_reliable";
String apiversion = "1.0";
String accesskey = "*******************************";
callApiSaveAsText(apiname, apiversion, accesskey);
}
public static void callApiSaveAsText(String apiname, String apiversion, String accesskey) {
String apiurl = "https://api.website-malware-removal.com/v" + apiversion + "/?api=" + apiname + "&accesskey=" + accesskey;
try {
URL url = new URL(apiurl);
HttpURLConnection connection = (HttpURLConnection) url.openConnection();
connection.setRequestMethod("GET");
int responseCode = connection.getResponseCode();
if (responseCode != 200) {
BufferedReader errorReader = new BufferedReader(new InputStreamReader(connection.getErrorStream()));
String errorResponse = errorReader.readLine();
JsonObject errorJson = JsonParser.parseString(errorResponse).getAsJsonObject();
if (errorJson.has("api_error")) {
System.out.println(errorJson.get("api_error").getAsString());
} else {
System.out.println("Unknown error");
}
return;
}
BufferedReader reader = new BufferedReader(new InputStreamReader(connection.getInputStream()));
StringBuilder response = new StringBuilder();
String line;
while ((line = reader.readLine()) != null) {
response.append(line);
}
reader.close();
JsonObject dataJson = JsonParser.parseString(response.toString()).getAsJsonObject();
int dataCount = dataJson.getAsJsonObject("metadata").get("data_count").getAsInt();
String exportFilename = apiname + ".json";
BufferedWriter writer = new BufferedWriter(new FileWriter(exportFilename));
writer.write(response.toString());
writer.close();
System.out.println("Successfully saved API json file - Data count: " + dataCount);
} catch (IOException e) {
e.printStackTrace();
}
}
}
using System;
using System.IO;
using System.Net;
using Newtonsoft.Json;
class Program
{
static void Main()
{
string apiname = "get_malware_patterns_reliable";
string apiversion = "1.0";
string accesskey = "28859139594f666f79c92bc86f0cd768";
CallApiSaveAsText(apiname, apiversion, accesskey);
}
static void CallApiSaveAsText(string apiname, string apiversion, string accesskey)
{
string apiurl = $"https://api.website-malware-removal.com/v{apiversion}/?api={apiname}&accesskey={accesskey}";
using (WebClient client = new WebClient())
{
try
{
string apidata = client.DownloadString(apiurl);
int responsecode = (int)client.ResponseHeaders["Status-Code"];
if (responsecode != 200)
{
dynamic apidata_decode = JsonConvert.DeserializeObject(apidata);
if (apidata_decode.api_error != null)
{
Console.WriteLine(apidata_decode.api_error);
}
else
{
Console.WriteLine("Unknown error");
}
return;
}
string exportfilename = $"{apiname}.json";
File.WriteAllText(exportfilename, apidata);
dynamic apidata_decode = JsonConvert.DeserializeObject(apidata);
Console.WriteLine($"Successfully saved API json file - Data count: {apidata_decode.metadata.data_count}");
}
catch (WebException ex)
{
Console.WriteLine(ex.Message);
}
}
}
}
Detecting the presence of malware in text data.
An example of code that reads the JSON data retrieved and stored by the above API and recursively checks the given text data for the presence of malware is shown below.
<?php
$code_to_detect = "Text code that maybe contains malware";
//Detect after removing white space.
$code_to_detect = str_replace(' ', '', $code_to_detect);
$code_to_detect = str_replace('\t', '', $code_to_detect);
$malware_patterns_data = json_decode(file_get_contents('get_malware_patterns_reliable.json'));
$malware_patterns = $malware_patterns_data->data;
foreach ($malware_patterns as $pattern){
if($pattern->is_regex != "1"){
$search_pattern = $pattern->without_whitespace_pattern;
$match = strpos( $code_to_detect , $search_pattern );
if($match !== false){
echo "May be malware contains in this code! Pattern ID:".$pattern->id." Malware probability:".$pattern->malware_probability."%\n";
}
}else{
$search_pattern = $pattern->raw_pattern;
preg_match_all($search_pattern, $code_to_detect, $match);
if(count($match[0])>0){
echo "May be malware contains in this code! Pattern ID:".$pattern->id." Malware probability:".$pattern->malware_probability."%\n";
}
}
}
?>import json
import re
code_to_detect = "Text code that maybe contains malware"
'''Detect after removing white space.'''
code_to_detect = code_to_detect.replace(' ', '')
code_to_detect = code_to_detect.replace('\t', '')
with open('get_malware_patterns_reliable.json') as file:
malware_patterns_data = json.load(file)
malware_patterns = malware_patterns_data['data']
for pattern in malware_patterns:
if pattern['is_regex'] != "1":
search_pattern = pattern['without_whitespace_pattern']
match = code_to_detect.find(search_pattern)
if match != -1:
print(f"May be malware contains in this code! Pattern ID: {pattern['id']} Malware probability: {pattern['malware_probability']}%")
else:
search_pattern = pattern['raw_pattern']
match = re.findall(search_pattern, code_to_detect)
if len(match) > 0:
print(f"May be malware contains in this code! Pattern ID: {pattern['id']} Malware probability: {pattern['malware_probability']}%")
cimport org.json.JSONArray;
import org.json.JSONObject;
import java.nio.file.Files;
import java.nio.file.Paths;
import java.util.regex.Matcher;
import java.util.regex.Pattern;
public class MalwareDetector {
public static void main(String[] args) {
String codeToDetect = "Text code that maybe contains malware";
//Detect after removing white space.
codeToDetect = codeToDetect.replace(" ", "").replace("\t", "");
try {
String malwarePatternsData = new String(Files.readAllBytes(Paths.get("get_malware_patterns_reliable.json")));
JSONObject malwarePatternsDataJson = new JSONObject(malwarePatternsData);
JSONArray malwarePatterns = malwarePatternsDataJson.getJSONArray("data");
for (int i = 0; i < malwarePatterns.length(); i++) {
JSONObject pattern = malwarePatterns.getJSONObject(i);
if (pattern.getInt("is_regex") != "1") {
String searchPattern = pattern.getString("without_whitespace_pattern");
int match = codeToDetect.indexOf(searchPattern);
if (match != -1) {
System.out.println("May be malware contains in this code! Pattern ID: " + pattern.getInt("id") + " Malware probability: " + pattern.getInt("malware_probability") + "%");
}
} else {
String searchPattern = pattern.getString("raw_pattern");
Pattern regexPattern = Pattern.compile(searchPattern);
Matcher matcher = regexPattern.matcher(codeToDetect);
if (matcher.find()) {
System.out.println("May be malware contains in this code! Pattern ID: " + pattern.getInt("id") + " Malware probability: " + pattern.getInt("malware_probability") + "%");
}
}
}
} catch (Exception e) {
e.printStackTrace();
}
}
}
using System;
using System.IO;
using Newtonsoft.Json;
using Newtonsoft.Json.Linq;
using System.Text.RegularExpressions;
class MalwareDetector
{
static void Main()
{
string codeToDetect = "Text code that maybe contains malware";
//Detect after removing white space.
codeToDetect = codeToDetect.Replace(" ", "").Replace("\t", "");
try
{
string malwarePatternsData = File.ReadAllText("get_malware_patterns_reliable.json");
JObject malwarePatternsDataJson = JObject.Parse(malwarePatternsData);
JArray malwarePatterns = malwarePatternsDataJson["data"].Value();
foreach (JObject pattern in malwarePatterns)
{
if (pattern.Value("is_regex") != "1")
{
string searchPattern = pattern.Value("without_whitespace_pattern");
int match = codeToDetect.IndexOf(searchPattern);
if (match != -1)
{
Console.WriteLine($"May be malware contains in this code! Pattern ID: {pattern.Value("id")} Malware probability: {pattern.Value("malware_probability")}%");
}
}
else
{
string searchPattern = pattern.Value("raw_pattern");
MatchCollection matches = Regex.Matches(codeToDetect, searchPattern);
if (matches.Count > 0)
{
Console.WriteLine($"May be malware contains in this code! Pattern ID: {pattern.Value("id")} Malware probability: {pattern.Value("malware_probability")}%");
}
}
}
}
catch (Exception e)
{
Console.WriteLine(e.Message);
}
}
}
cApi result errors
If the API is successful, JSON data is returned with response code 200.
| HTTP responce code | api_error |
|---|---|
| 403 | Api not found |
| 403 | Accesskey not suplied |
| 403 | Accesskey not found |
| 403 | Paid user not found |
| 403 | Too many api access |
| 500 | Server error |
| 500 | JSON data is empty |
Limitation
[API limitations]
-API data is updated up to once every 24 hours. Therefore, the data that can be retrieved by the API once a day is the most recent data available.
-Each API can only be called once every 30 seconds maximum. Also, data is only updated once a day. For this reason, do not call the API every time you use the data.
Call the API once a day, e.g. with CRON JOB, to record the data in a database or text file, and then call the data on your own server for use.
[Restrictions in terms and conditions]
-It is prohibited to disclose or make the data acquired by the API available for viewing to unspecified parties.
-The data acquired by the Malware Detection API may not be used for purposes other than malware detection.
-Selling data to third parties is not permitted (providing software or services using the data to third parties for a fee is permitted).
-If you send a query that places an excessive load on our servers, we may temporarily block access to the API.
